Search posts by keywords:
Filter posts by author:
Related Reports
Related NEAT Reports
Other blog posts
posted on Jul 18, 2017 by Mike Smart
Every day the sheer amount and complexity of cybersecurity information that security analysts are required to sift through increases. Analysts arrive at the start of each day, catch-up on recent attacks and research cybersecurity news, and are thrown into analyzing security incidents: going down the rabbit hole of reviewing data flows, finding outliers, investigating IPs, searching through both internal and external structured and unstructured data sources, etc. All this work compounds the skills shortage that the cybersecurity services industry faces and the fatigue that security analysts endure.
Enter IBM’s Cognitive Security.
IBM has been training its cognitive analytics solution, Watson, to understand the ‘language’ of cybersecurity.
Watson ingests data from a massive range of material spanning structured data from the likes of its X-Force Exchange and partner data every 5-minutes; crawling unstructured data such as security blogs every hour; and every 1-3 days pulling in millions of documents from across the web. Data is then filtered, removing unnecessary information using machine learning capabilities, for which Watson then extracts relevant information and annotating it for security analysts.
Building up its knowledge corpus, Watson is able to automate the analysts’ work of searching for data, linking into QRadar. Security analysts using QRadar are provided with a set of insights on a threat, and by pressing a single button can view a knowledge graph that details the relationships between devices, threats, files, IPs, etc. and then dives into more detail.
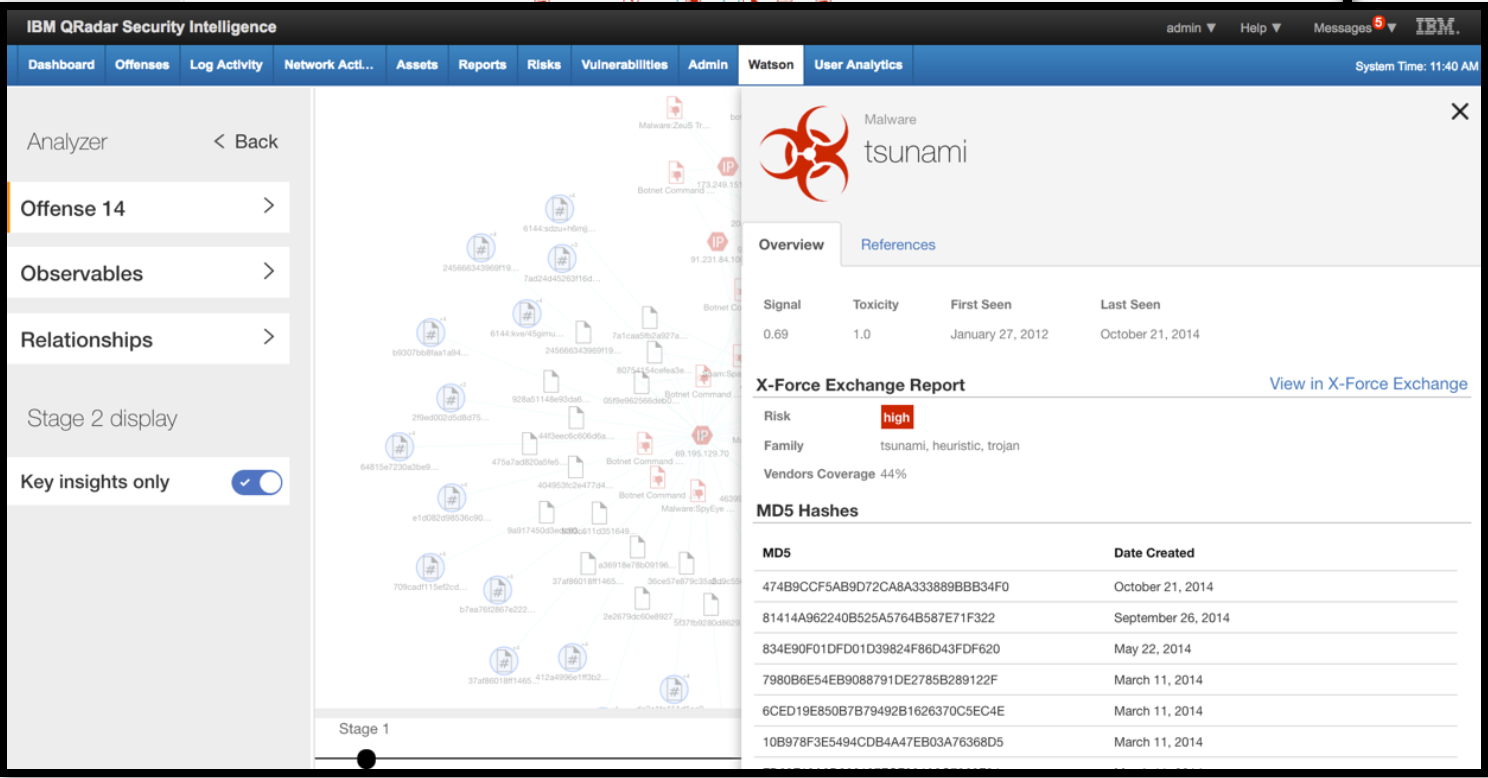
Watson’s knowledge graph and threat report
IBM has stated that the use of this cognitive power can speed up the analysis of a security threat from 1 hour to less than 1 minute, adding more insights than the analyst would ever be able to search.
Security analysts can rate the analytics performed by Watson, and with IBM increasing the amount of information being ingested into the knowledge corpus, the quality of the insights provided is improving fast. Initial feedback on the Watson for cybersecurity beta program set up in December 2016 to 40 clients wasn’t completely positive, but with bi-weekly calls the quality of results from Watson increased rapidly.
By shifting analysts’ work focus from searching through multiple sources for data, these cognitive solutions are reducing the time spent on L1 and L2 activities: not only is there a shortage of cyber analysts, but the deployment of Watson for Cybersecurity makes the work less grunt.
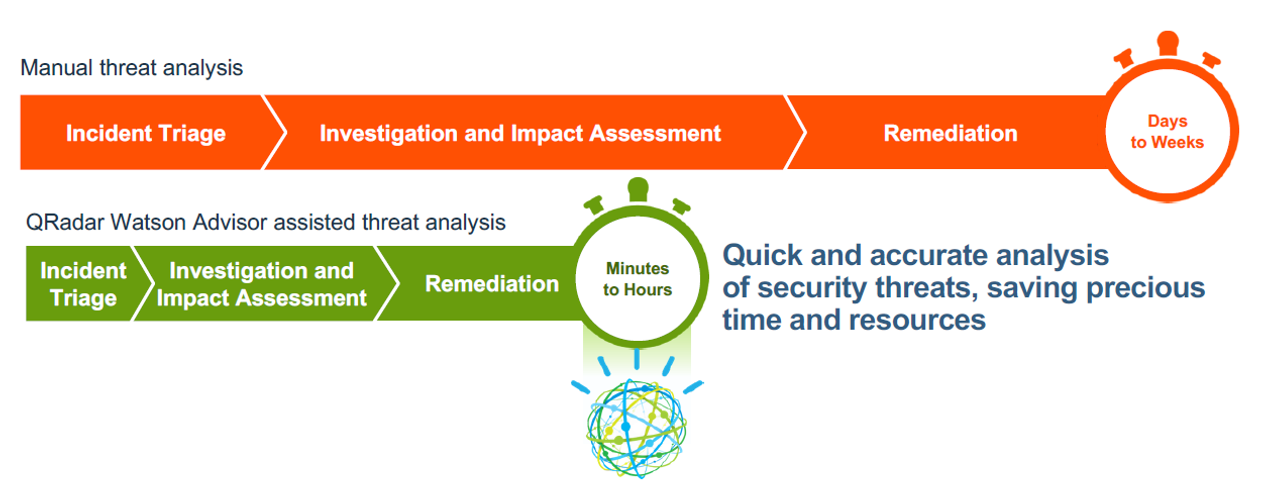
The difference in analyst time spent using traditional research and with Watson
Where else is IBM taking cognitive security?
By teaching Watson the ‘language’ of security, IBM has built two solutions that help its cyber analysts and clients interact.
The first is Security Services Virtual Analyst, launched in October 2016, which acts as a chatbot in the client’s MSS portal. The chatbot answers common questions from clients up to 50 times faster than waiting for a security analyst.
The second, Project Havyn, allows security analysts to talk directly to QRadar to perform actions more efficiently.
IBM has recently linked QRadar Advisor with Watson to Resilient Systems, the incident response solutions vendor it acquired in March 2016. With this, the Watson QRadar app can directly send on threat information to Resilient’s QRadar app, for Resilient to have the best information upon which to act and stop the attack. In future, it is not out of the range of possibility for vendors to look to implement a cognitive solution that can both analyze threats and also immediately perform remediation actions such as patching vulnerabilities.
With the use of IoT about to accelerate, and the increasing complexity and scale of cyberattacks already apparent, the importance of the use of these cognitive technologies in cybersecurity should not be underestimated.
