posted on May 16, 2017 by Mike Smart
Last Friday morning, the largest ransomware cyber attack infected an unprecedented number of machines across organizations worldwide. The ransomware named WannaCry demanded $300 in Bitcoins to be paid in three days, otherwise the ransom would double. If no payment was made after seven days, data would be deleted forever.
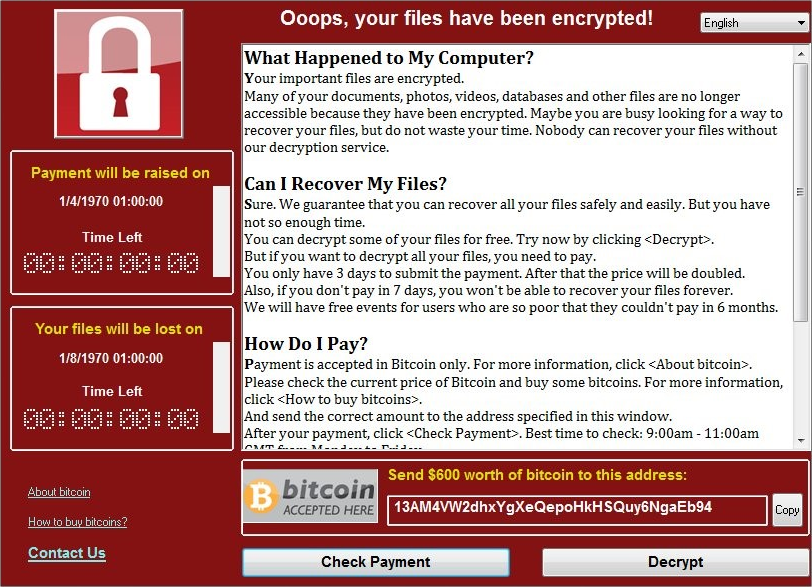
WannaCry ransom message
Each time this ransomware infected a new computer it tried to connect to a domain; if it could not reach the domain, WannaCry continued to spread. To aid its spread, WannaCry utilized a tool known as EternalBlue to identify and use file sharing protocols on the infected systems to spread. EternalBlue is a hacking tool developed by the NSA then stolen by a group called Shadow Brokers and dumped online in April.
With the online dump of the vulnerability, known as MS17-010, Microsoft went about producing and releasing a security patch to fix the vulnerability, quickly pushing the update live to its current operating systems. Unfortunately for some, operating systems that had been EoL’d before the attack, namely Windows XP, did not have a security patch released initially as Microsoft usually charges to provide custom support agreements for old version of Windows.
Organizations hit that have in part remained on XP include Telefónica, the NHS, FedEx, Renault, and Police and petrol stations in China.
Advice for ransomware is to:
- Isolate the system
- Power off
- Secure any data backups
- Contact law enforcement
- Change account passwords.
The FBI had previously released a controversial statement saying they often advise people to pay the ransom, though it does state that paying is no guarantee of getting data back.
The trouble with any advice to pay WannaCry is the mechanism it has to release infected systems. WannaCry has no process to uniquely identify which infected machines have paid the ransom and therefore the likeliness that any infected machines will be released by the attacker is low. Nevertheless, the hackers’ bitcoin wallets have received more than 230 payments totaling more than $65k.
So what can be done about WannaCry and other similar ransomware?
After two days, Microsoft released a patch for Windows XP to fix the vulnerability.
Before this, the attack had been slowed by a security researcher who analyzed the code of WannaCry and detected the domain kill switch it had been attempting to connect to. By registering this domain (for less than $11), newly infected systems received the kill switch and did not go on to spread the ransomware. However, since this, a second version of WannaCry was released without this kill switch.
Organizations should be looking towards their IT service providers to mitigate the threat.
In the immediate timeframe, clients should look towards their service providers to download and apply all applicable OS security patches and antivirus updates and look at what data DR systems can restore.
Moving forwards, organizations should be looking with their IT service providers at:
- Performing a cybersecurity vulnerability analysis to assess the current state of affairs, discover the organization's crown jewels, and close vulnerabilities
- Developing business continuity plans to ensure even if/when a cyberattack occurs, the organization knows how to react and reduce the impact
- Developing cybersecurity training programs to reduce the chance staff will download malware/ransomware.
As part of a wider conversation, if an enterprise has business critical infrastructure that remains on outdated OS’s, it should be looking at how these systems can be secured. These systems could be upgraded to more current OS’s, or if legacy processes or applications prevent this move, perhaps look at other methods of protecting these systems such as air gapping the infrastructure or even paying for Microsoft’s extended service agreement.
In the case of the NHS, at end 2016, incredibly 90% of NHS Trusts were still using Windows XP in some capacity – yet last year, the U.K. Government Digital Service decided not to extend a £5.5m one-year support deal that would have included security patches. We imagine there are some red faces at GDS. Decisions like this in not extending this support deal have now had a huge impact in some areas of the NHS, including in some areas causing delays in the delivery of life-saving services. There are clearly lessons to be learned in both the public and private sector about managing old estates.
